2025 SK Telecom Breach
On April 18, 2025, South Korea's largest mobile carrier, SK Telecom (SKT), faced a significant cybersecurity incident. The company's core network was compromised in an attack that targeted its Home Subscriber Server (HSS), a central component managing subscriber data.
SKT later confirmed that the incident involved a "large-scale leak of data due to malware" detected on the day of the attack. The compromised information included sensitive Universal Subscriber Identity Module (USIM) data – the data associated with SIM cards used by mobile subscribers. While SKT stated that personal names and financial account details were not exposed, the USIM data itself is critical for network authentication and services.
The scale of the breach was considerable, impacting a vast number of SKT's subscribers, estimated to be around 25 million – essentially their entire user base. The incident was quickly recognized as a major event in the history of Korean telecommunications, prompting significant concern. Following the announcement, SKT's stock experienced a decline.
In response, SKT issued a public apology, accepting responsibility for potential impacts on customers. They initiated immediate measures, offering free SIM card replacements and launching enhanced protection services for all users to mitigate potential risks.
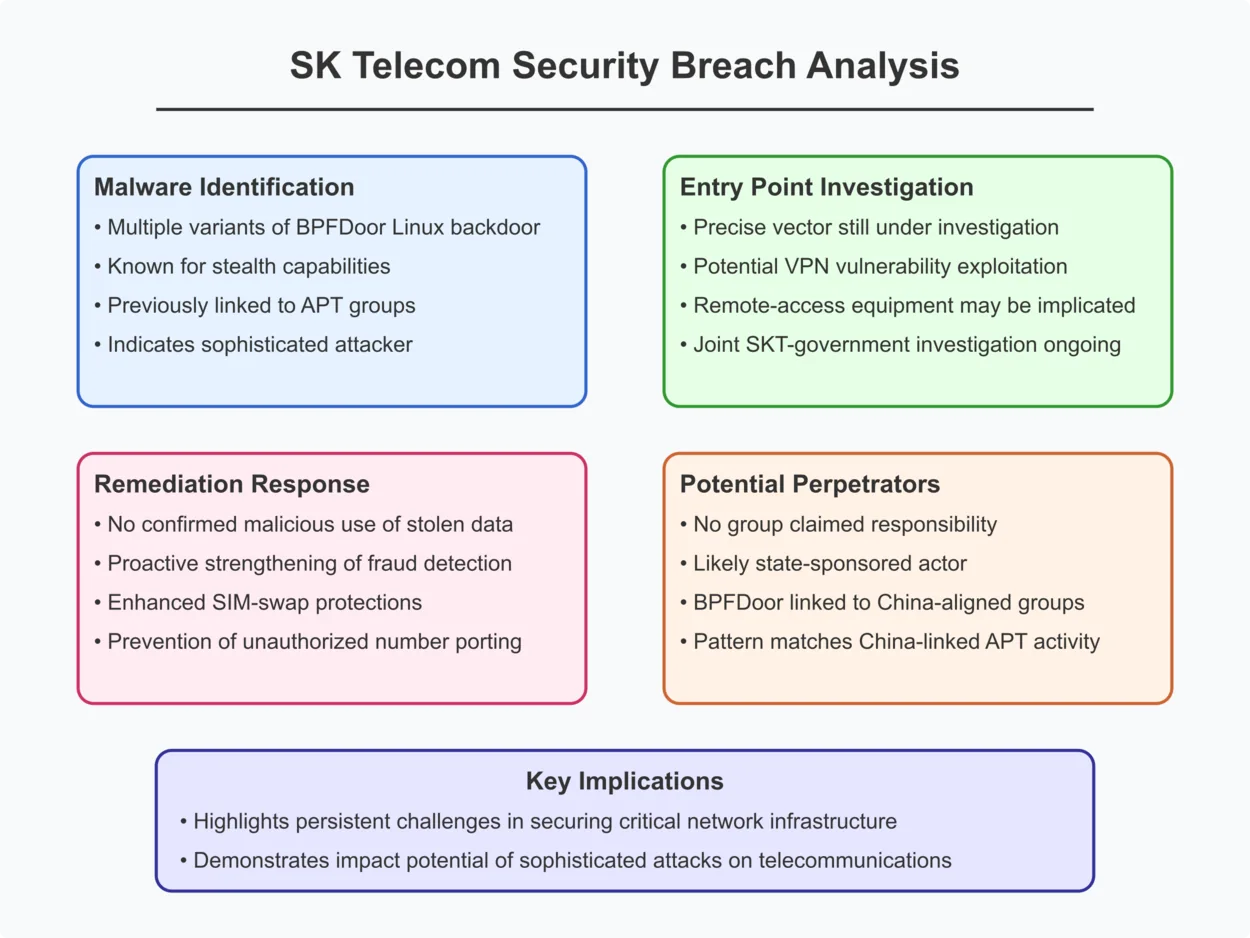
Technical analysis provided more insight into the nature of the attack. Investigators believe sophisticated malware was used to infiltrate SKT's internal network. Security reports indicate that a malicious program was identified within SKT's systems on the night of April 19, 2025, prompting its immediate removal and isolation of affected equipment.
Table of Contents
Technical Details of the SK Telecom Breach
Forensic examination by government agencies identified the intrusive software as multiple variants of a Linux backdoor known as BPFDoor. This type of malware is noted for its ability to remain hidden and has been associated in previous incidents with advanced persistent threat (APT) groups, suggesting a highly capable attacker.
The precise entry point used by the attackers is still under investigation, with some security experts suggesting a vulnerability in VPN or remote-access equipment may have been exploited. A joint SKT and government investigation is ongoing to fully understand the breach.
While there has been no confirmation of the stolen data being used maliciously so far, SKT proactively strengthened its fraud detection systems and expanded SIM-swap protections to prevent unauthorized porting of mobile numbers.
The SK Telecom incident highlights the persistent challenges in securing critical network infrastructure and the potential impact of sophisticated cyberattacks on a large scale. It underscores the need for continuous vigilance and robust security measures in the telecommunications sector.
Potential Perpetrators
No group immediately stepped forward to claim responsibility for the sophisticated infiltration, leaving investigators to piece together clues in the digital dust. Cybersecurity analysts quickly noted hallmarks suggesting a highly skilled, potentially state-sponsored actor. The appearance of the BPFDoor backdoor, a tool previously linked to hacking groups aligned with Chinese interests, became a focal point of speculation. Adding to this, reports from a Taiwanese security firm highlighted a pattern of China-linked advanced persistent threats (APTs) exploiting vulnerabilities in VPN software globally, including within the telecommunications sector – a potential parallel that fueled the ongoing inquiry. While South Korean authorities have remained cautious in official attribution, a comment from a Deputy Chair at the Personal Information Protection Commission hinted at a belief that the leak originated directly from SKT's main servers, seemingly pushing back against any suggestion otherwise. The focus of the government's investigation remains on pinpointing whether the breach stemmed from an insider threat or sophisticated external actors, and critically, whether SKT's security measures on its vital HSS servers were adequately robust.
Who is SK Telecom?
To understand the magnitude of this event, one must recognize SK Telecom's place in the fabric of South Korea. As the flagship wireless carrier and a key entity within the powerful SK Group, SKT isn't merely a mobile provider; it's a cornerstone of the nation's digital infrastructure. Commanding roughly half of the domestic mobile market, with a subscriber base of 23 to 25 million in a country of 50 million, SKT holds immense influence. The company has long been at the forefront of mobile technology, pioneering advancements from 3G to 5G, and its service portfolio extends across broadband, IoT, and digital media. As a publicly traded company with significant revenue, its operational health is tied to the national economy.
More crucially, SKT serves as a critical national asset, providing the underlying network capacity for smaller carriers and acting as a fundamental platform for countless financial and identity verification services that everyday citizens rely upon. In essence, SKT is South Korea's incumbent telecom giant, a figure comparable in its national significance to major carriers in other large economies.
Customer Impact - How are SK Telecom subscribers affected?
For the millions of SKT subscribers, the confirmed details of the breach brought a mix of relief and anxiety. SKT maintained that core personal identifiers like names, addresses, or financial data were not exposed.
However, attackers did obtain USIM-related information, including phone numbers and critical International Mobile Subscriber Identity (IMSI) values. This combination, while not granting direct access to bank accounts, is sufficient in theory to clone SIM cards or intercept those crucial two-factor authentication codes sent via SMS that many services use. Encouragingly, IMEI device identifiers were reportedly not compromised, and SKT's investigation has, as of now, found no concrete evidence of the stolen data being misused. Nevertheless, the inherent risk of SIM-swap fraud, a tactic where criminals take control of a victim's phone number to access accounts, was enough to generate significant concern among the customer base.
SKT responded by offering free SIM card replacements to all affected subscribers. The uptake was swift; within days, hundreds of thousands had swapped their cards, and millions more booked appointments online. However, the sheer scale of the user base quickly exposed a practical challenge: inventory shortages. Reports indicated SKT had a limited stock of spare SIMs and faced a scramble to procure millions more to meet demand. This logistical hurdle, coupled with the underlying anxiety, contributed to customer churn.
Media outlets highlighted that tens of thousands of subscribers opted to cancel or port their service to rival carriers in the immediate aftermath, a notable surge compared to previous months. While SKT's network and services generally remained operational, the company took the step of suspending new customer sign-ups while it focused on managing the crisis and reinforcing security. The breach undeniably eroded customer trust, creating widespread unease even without direct compromise of financial data or passwords.
Public and Government Response
The fallout from the SKT breach quickly escalated to the highest levels of government and public discourse. South Korea's Ministry of Science and ICT formally ordered SKT to halt new customer acquisitions at its retail locations until sufficient SIM card stock and enhanced protections were in place. SKT's CEO publicly acknowledged the severity, labeling it "the worst hacking case in telecom history" for the company and pledging a full effort to restore confidence. During a parliamentary hearing, the CEO faced sharp questions, confirming the date of the attack's detection and admitting to delays in officially notifying relevant authorities. The Acting President personally mandated a government review of SKT's handling of the incident within hours of it becoming public.
Government agencies mobilized to contain the fallout and bolster defenses. The Personal Information Protection Commission launched an investigation specifically to assess whether SKT had maintained adequate security safeguards on its USIM servers. Financial regulators convened meetings with banks and card issuers, issuing warnings and guidance on monitoring for potential SIM-swap fraud. Law enforcement and the National Assembly also became involved, assisting SKT in developing its SIM Protection service and signaling a potential push for stronger cybersecurity legislation. Public advisories were issued, cautioning citizens about circulating phishing scams leveraging the incident, and SKT itself clarified how it would communicate official information to customers.
The incident garnered relentless media attention, both domestically and internationally, keeping the breach's scope and the need for preventative measures in the public eye. Social media became a hotbed of rumors, prompting SKT to publicly debunk false claims about stolen data being sold online. Beyond immediate technical responses, customer advocacy groups and lawmakers began exploring broader protections, including proposals to waive contract penalties for customers wishing to switch providers due to the breach. Meanwhile, some SKT subscribers took legal action, filing class-action lawsuits seeking compensation for the distress and inconvenience caused by the security failure.
Actions Steps to Protect Yourself from the Breach
Responding to a cybersecurity incident requires decisive action. For individuals affected by the SK Telecom data breach, experts and authorities advise implementing the following protective measures:
1. Secure Your SIM Card: The primary recommendation is to obtain a new SIM card. SK Telecom is providing free replacements for all affected subscribers. This can typically be arranged by making an appointment or visiting an SKT retail store or authorized kiosk. Replacing the physical SIM card invalidates the compromised authentication keys that were potentially exposed during the breach, thereby mitigating a key risk factor.
2. Activate SIM Protection Services: Regardless of whether you replace your physical SIM, it is strongly advised that all SKT customers enroll in the company's USIM Protection Service. This service functions by electronically binding your phone number to your current SIM card, creating a safeguard against unauthorized SIM porting or swapping attempts. Official statements indicate that this service offers a level of defense against illicit activity comparable to that of physically replacing the SIM. Enrollment is generally accessible through SKT's online platforms or their official mobile application.
3. Exercise Caution Regarding Unsolicited Communications: Be highly suspicious of unexpected text messages or emails that reference the SKT SIM replacement process or related security measures. SKT has issued warnings that fraudulent "smishing" (SMS phishing) and phishing attempts are likely circulating, attempting to exploit the situation. Legitimate notifications and instructions from SKT concerning this breach will be communicated through official, verified channels, such as messages originating from the designated service number (e.g., 114) or within the secure environment of the official SKT mobile application. Avoid clicking on links or sharing personal or SIM-related information in response to any unsolicited messages.
4. Reinforce Account Security: As a precautionary step, it is prudent to re-authenticate your login sessions for critical mobile applications, including banking, email, and any digital identity or authentication apps (such as the PASS app). Monitor your financial accounts diligently for any unusual or unexpected activity. Review and update passwords for important online accounts. Where available, enable multi-factor authentication (MFA), prioritizing methods that do not rely on SMS delivery, such as dedicated authenticator applications, as SMS-based codes can potentially be intercepted in SIM-swap scenarios.
5. Consult Official Information Sources: Stay informed about the incident and ongoing protective measures by referring exclusively to official announcements from SK Telecom, available on their verified website and social media platforms, as well as reports from credible news organizations. Authorities may also establish dedicated hotlines or online resources to provide specific guidance and allow individuals to check if their account was directly affected. SKT and relevant government ministries are maintaining support channels and frequently asked questions sections to assist subscribers through the SIM replacement and protection enrollment processes.
Implementing these recommended actions will substantially reduce the risk of potential fraud or unauthorized access stemming from the breach. While the compromised data alone is not sufficient for immediate financial account depletion, replacing the SIM and enabling protective services significantly complicates attempts at unauthorized SIM-swap attacks. Maintaining vigilance against related social engineering tactics, such as criminals impersonating legitimate entities, remains essential.